Encryption without magic, risk management without pain

In-depth technical inquiry about application-level encryption. How crypto helps to narrow down significant risks to controlled attack surfaces, enables managing the risk efficiently and elegantly, how tools and algorithms sit in a broader context of managing infrastructure-wide risks associated with handling sensitive data.
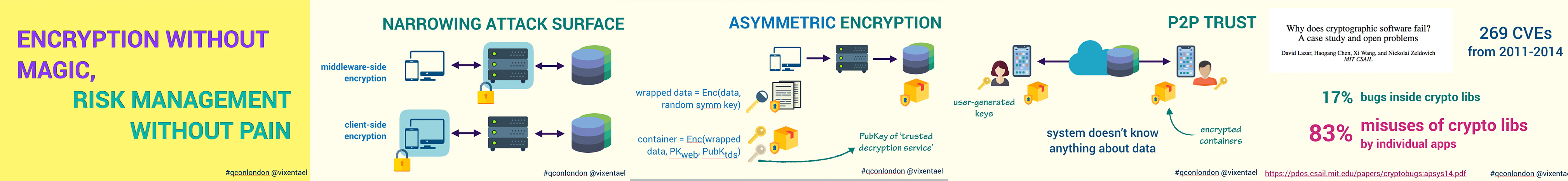
We discuss client-side, middleware-side and proxy-side encryption. End-to-end encryption, Zero knowledge, Zero trust systems.
Click to read slides.Points we cover
- What is attack surface, how cryptography helps to narrow it.
- Simple crypto-systems, but significant downsides.
- Middleware-side encryption: protecting data in web-based infrastructures.
- Client-side encryption: trust to mobile apps and code execution. E2EE. ZKA. ZKP.
- Echelonization, and traditional techniques.
Read talk transcript on Codemotion site.
Watch ENG 📺 [QCon London]
Watch RU 📺 [Security BSides]
Click to read slides.Presented at ✨
QCon London 18 London, UK, 5-7 March 2018
Security BSides Ukraine Kyiv, Ukraine, 21 April 2018
Codemotion Milan Milan, Italy, 29-30 November 2018