10 lines of encryption, 1500 lines of key management
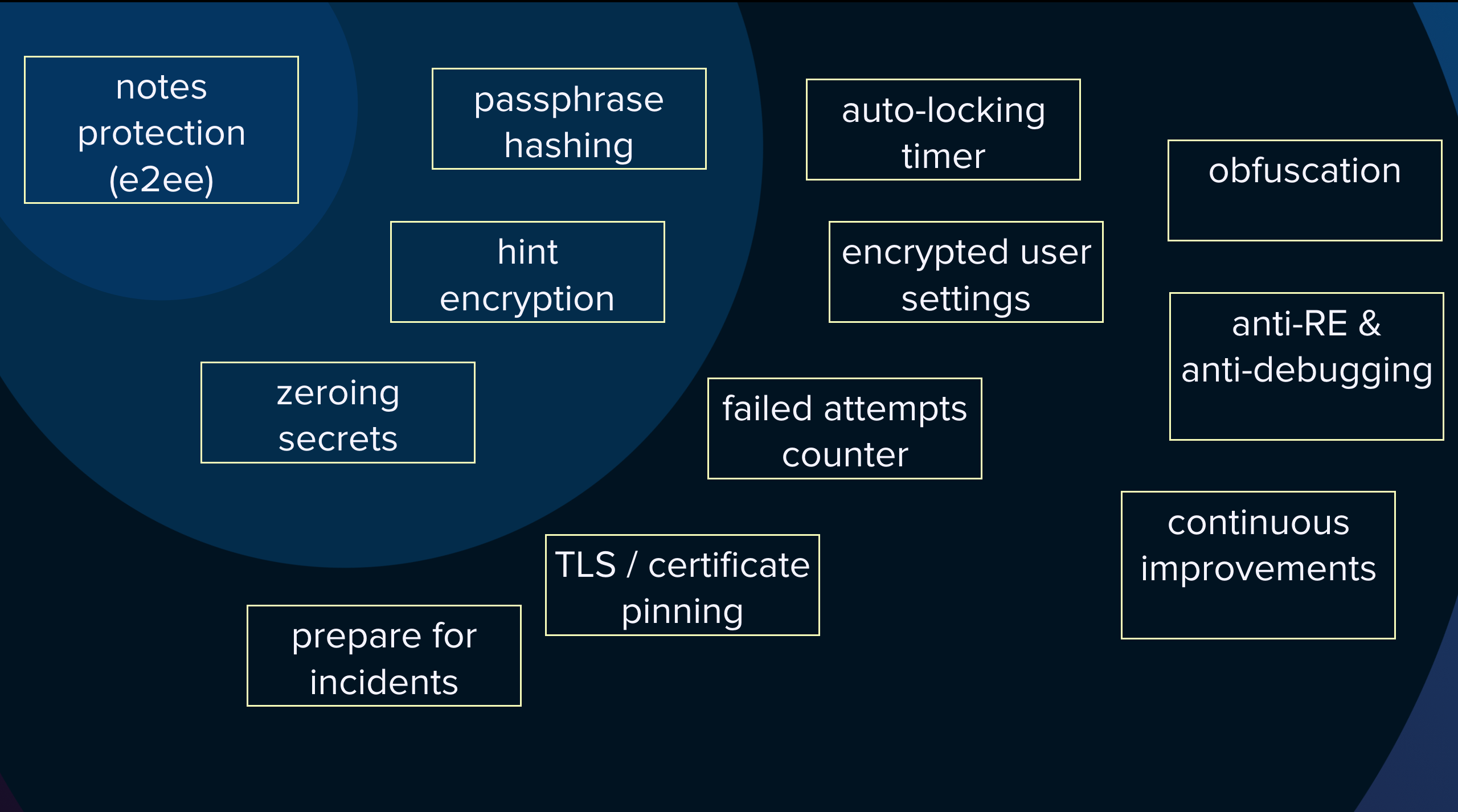
The real case about Bear note taking the app that decided to implement convenient note encryption and note locking for their existing user base. But finding a balance between usability, security and mobile platforms’ restrictions is complicated.
We start with the security design scheme, then select the proper encryption library, then implement the flow, and prepare for incidents. Now — think about it — cryptography is only chapter 3 in OWASP MASVS (8 chapters in general). Even the best cryptography will fail if basic security controls are badly implemented.
Click to read slides.Points we cover
- the difference between “locking” and “encrypting”,
- the difference between a password and encryption key,
- how to sync passwords between devices, what exactly to store in keychain/keystore,
- how to use proper cryptography (AES CBC or AES GCM, random salt? IV? padding? what a hell is this mess),
- how to use biometrics (we don’t want to bother user, let’s use biometric keychain, but what if users will change their fingerprints — shall we invalidate all passwords?),
- updating encryption version (imagine, vulnerability is discovered in our library or app — how to update cipher, and softly migrate users to the new cipher, if users don’t even have a clue that encryption was versioned).
In the end, this is only one simple JIRA ticket “let’s encrypt the notes” from the eyes of security software engineer :)
Read a technical blogpost “Implementing End-to-end Encryption in Bear App” about details of implementation.
Watch ENG 📺
Click to read slides.Watch RU 📺
Click to read slides.Presented at ✨
FrenchKit Paris, France, 7-8 October 2019
RSConf Minsk, Belarus, 9-11 August 2019
CocoaHeads Kyiv conference Kyiv, Ukraine, 28 July 2019