Cryptographic protection of ML models

Imagine a system that operates with ML models. These models are unique and work with user-generated content better than anyone else.

Imagine a system that operates with ML models. These models are unique and work with user-generated content better than anyone else.
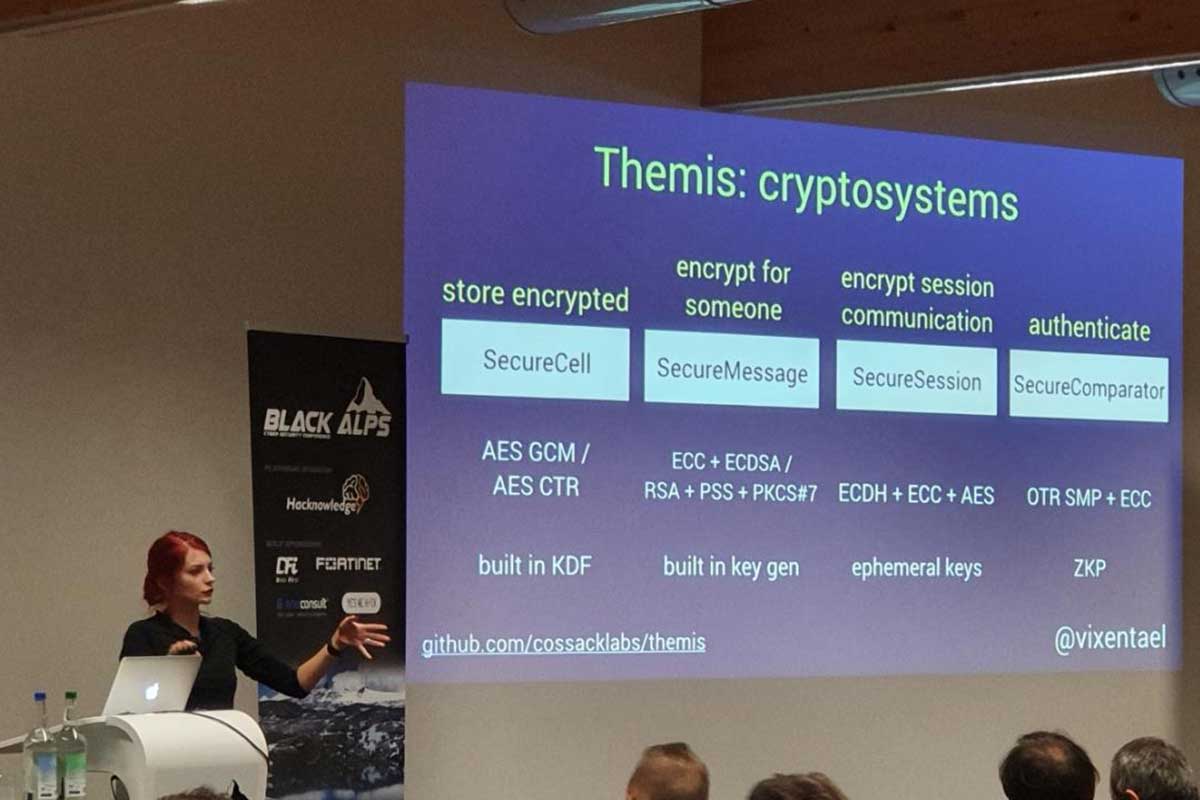
Maintaining cross-platform cryptographic library is a journey full of unexpected bugs, language-specific hacks, difficult decisions and endless struggle to make developer-facing APIs easy-to-use and hard-to-misuse.
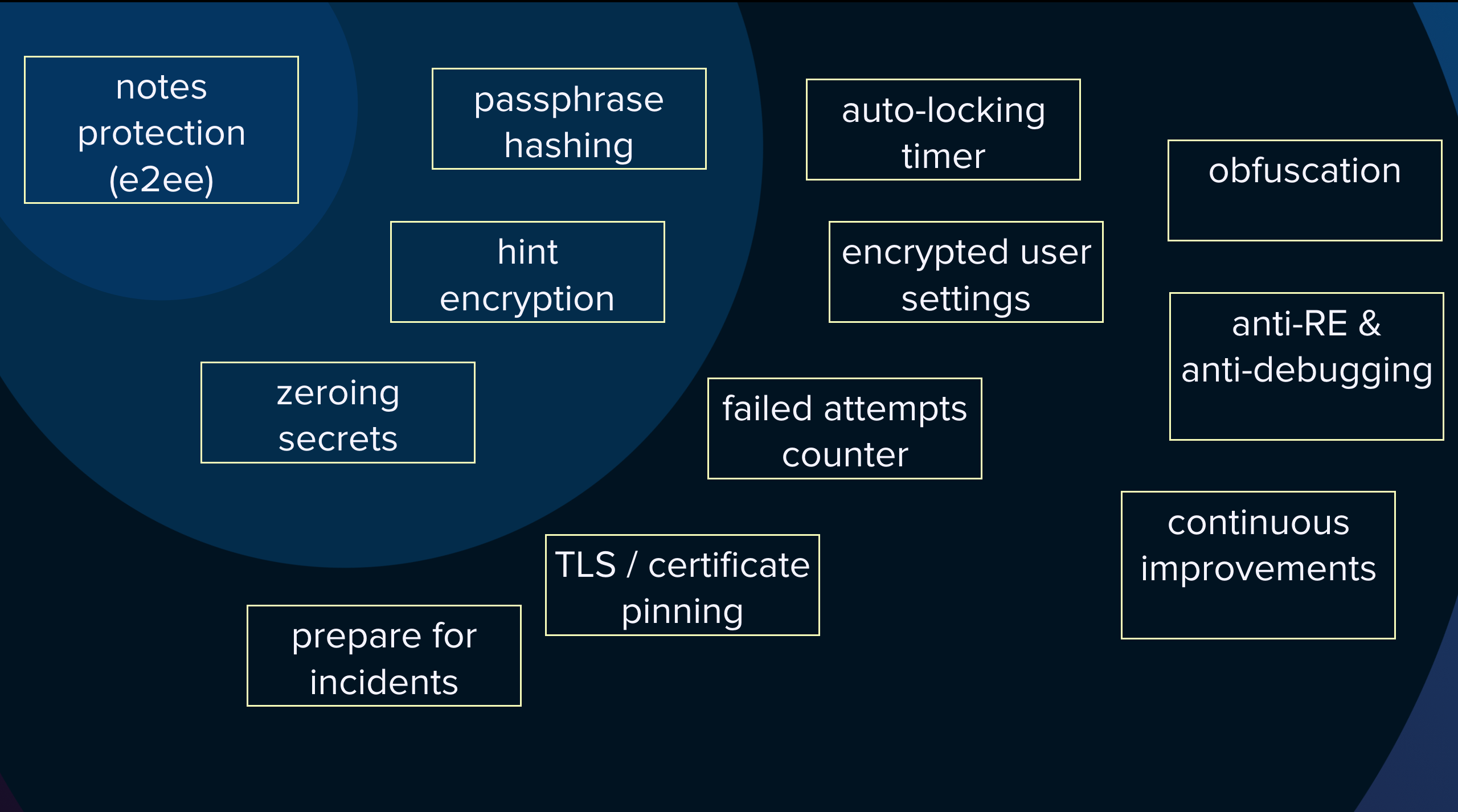
The real case about Bear note taking the app that decided to implement convenient note encryption and note locking for their existing user base.
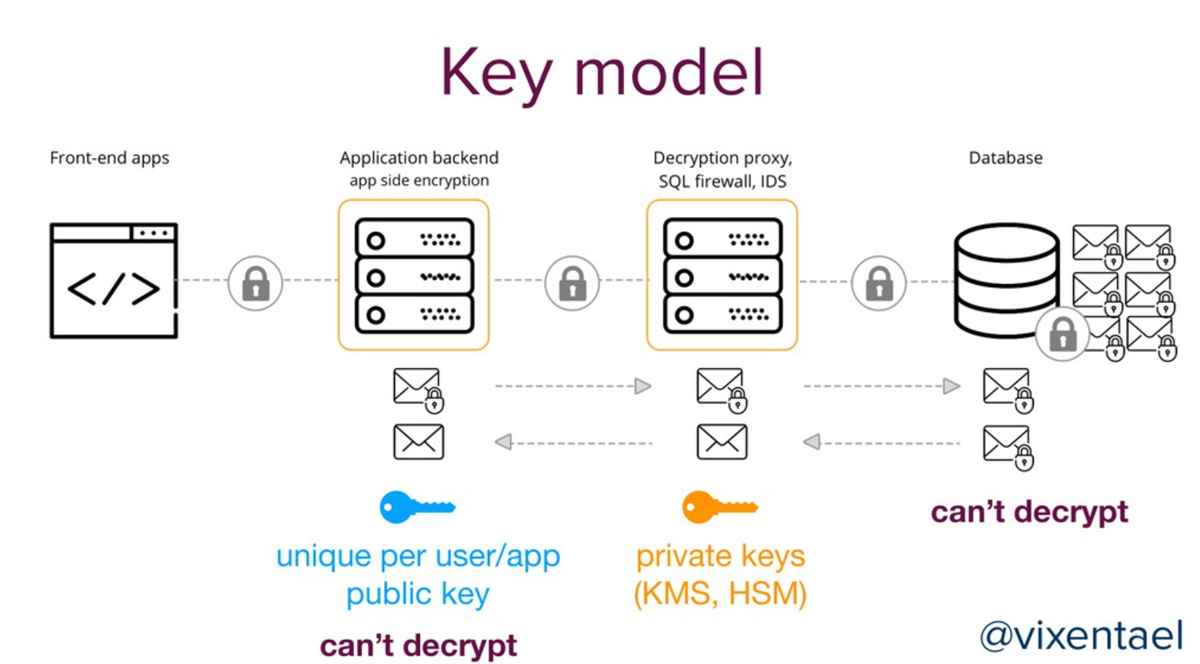
It comes to no surprise that any micro-services, any security controls you use to build applications – will eventually be broken (or fail).

Modern apps are multi-components, and most data leaks are caused by poor architectural decisions.