Cryptographic protection of ML models

Imagine a system that operates with ML models. These models are unique and work with user-generated content better than anyone else.

Imagine a system that operates with ML models. These models are unique and work with user-generated content better than anyone else.
We’re speaking about cryptography and explain why base64 is our favourite cipher!

We’ll talk about “boring crypto”: why developers shouldn’t spend time learning all the details of crypto-algorithms (or invent new ones).
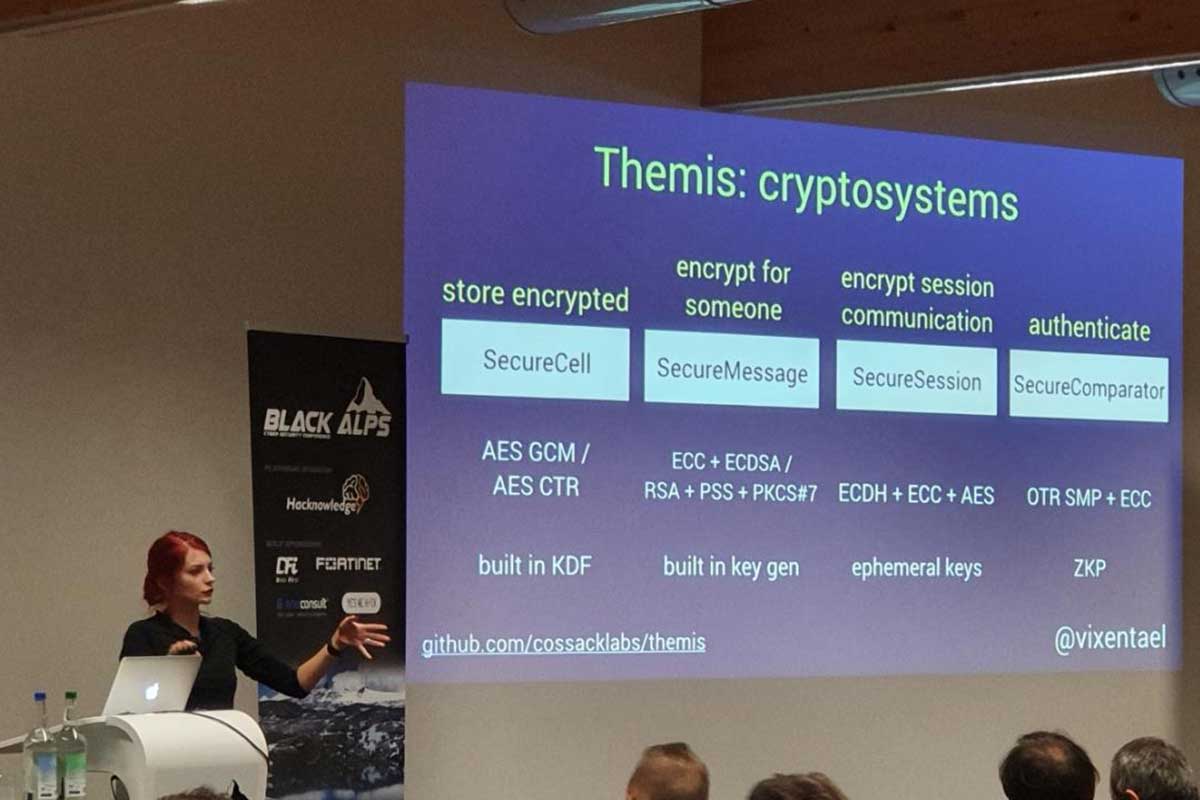
Maintaining cross-platform cryptographic library is a journey full of unexpected bugs, language-specific hacks, difficult decisions and endless struggle to make developer-facing APIs easy-to-use and hard-to-misuse.
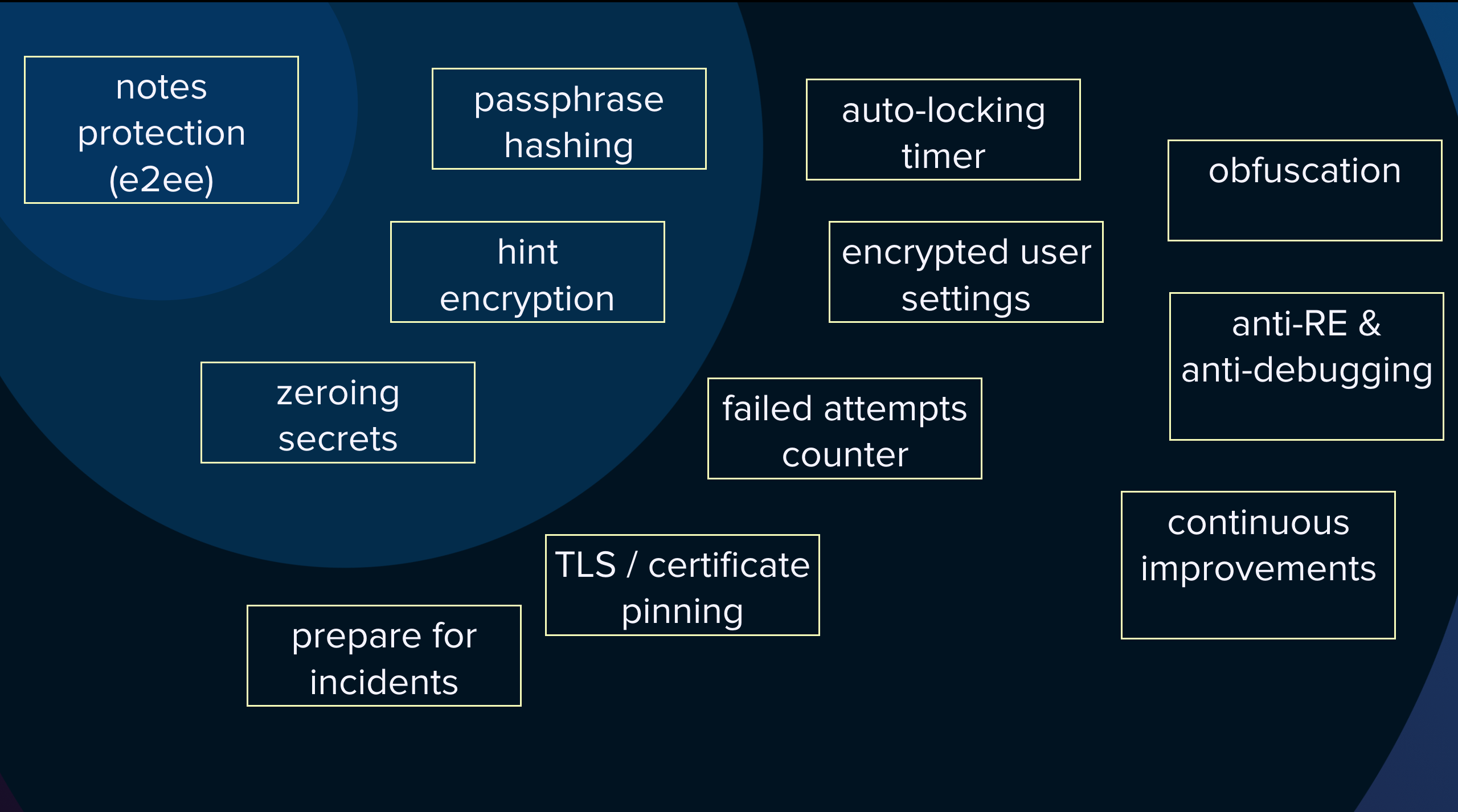
The real case about Bear note taking the app that decided to implement convenient note encryption and note locking for their existing user base.