Defense in depth: trench warfare principles for building secure distributed applications
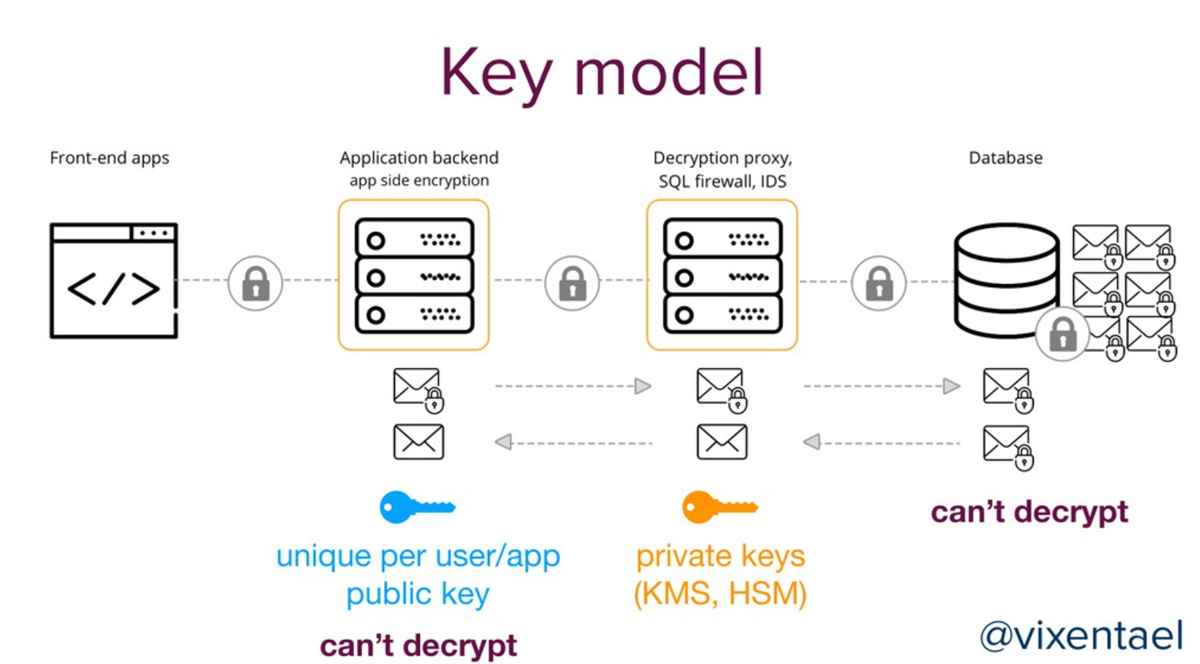
It comes to no surprise that any micro-services, any security controls you use to build applications – will eventually be broken (or fail).

It comes to no surprise that any micro-services, any security controls you use to build applications – will eventually be broken (or fail).