Defense in depth: trench warfare principles for building secure distributed applications
It comes to no surprise that any micro-services, any security controls you use to build applications – will eventually be broken (or fail).

It comes to no surprise that any micro-services, any security controls you use to build applications – will eventually be broken (or fail).

Apple made many announcements on WWDC 2019 about cryptography, cybersecurity and privacy.

I was co-organizing CyberKids event during NoNameCon cyber security conference in Kyiv, Ukraine, May 2019.

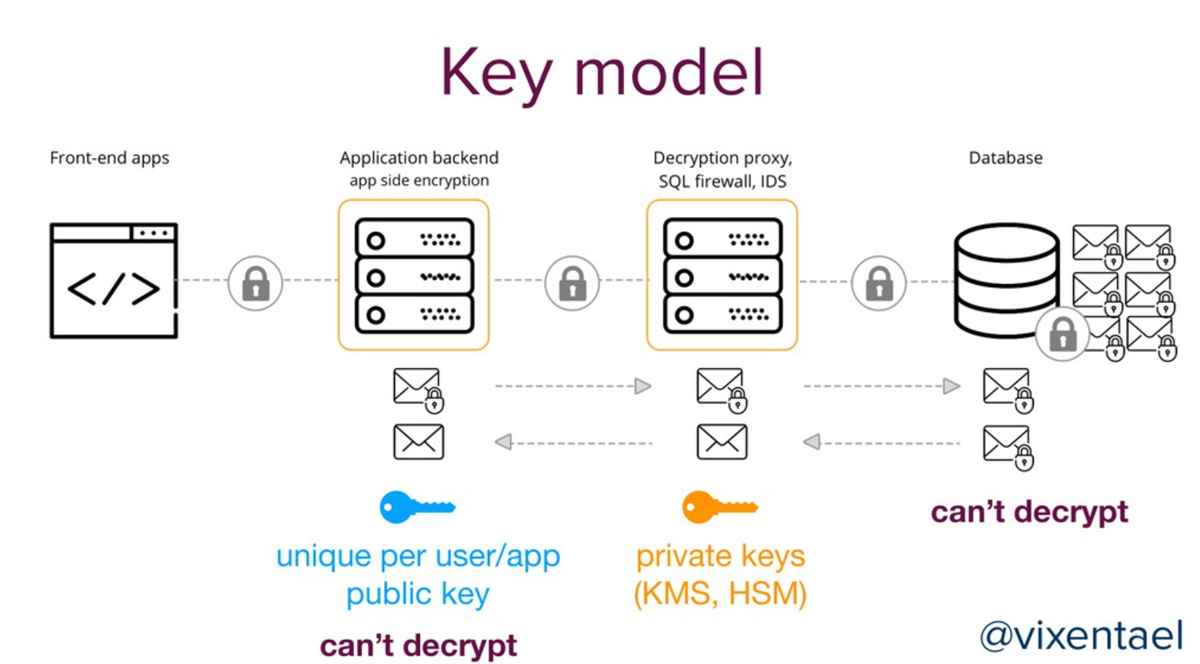
Modern apps are multi-components, and most data leaks are caused by poor architectural decisions.

The essay I wrote for De Programmatica Ipsum magazine about secure software development and the mindset gap between the world of product makers and the world of security people.

I’m working at Cossack Labs on data protection & encryption tools. Some are free, some are proprietay, but all of them are easy-to-use & hard-to-misuse, and do protect data.
Visit site