Cryptographic protection of ML models

Imagine a system that operates with ML models. These models are unique and work with user-generated content better than anyone else.

Imagine a system that operates with ML models. These models are unique and work with user-generated content better than anyone else.
OWASP Zhytomyr meetup “Security on your project from scratch”: risks analysis, building SSLDC, working with the development team and checklists.
A live episode with live Q&A of iOS App Security by Vincent Pradeilles and Anastasiia Voitova.
Semi-fun semi-serious podcast episode where Jeroen Leenarts asks me questions about life, education, programming, and security.
Russian-speaking podcast about software engineering lead by engineers all over the world.

We had a lot of fun discussing the latest mobile app security topics from the eyes of people that build secure apps and help others to build secure apps: iOS14 privacy features, security.
We’re speaking about cryptography and explain why base64 is our favourite cipher!

We’ll talk about “boring crypto”: why developers shouldn’t spend time learning all the details of crypto-algorithms (or invent new ones).
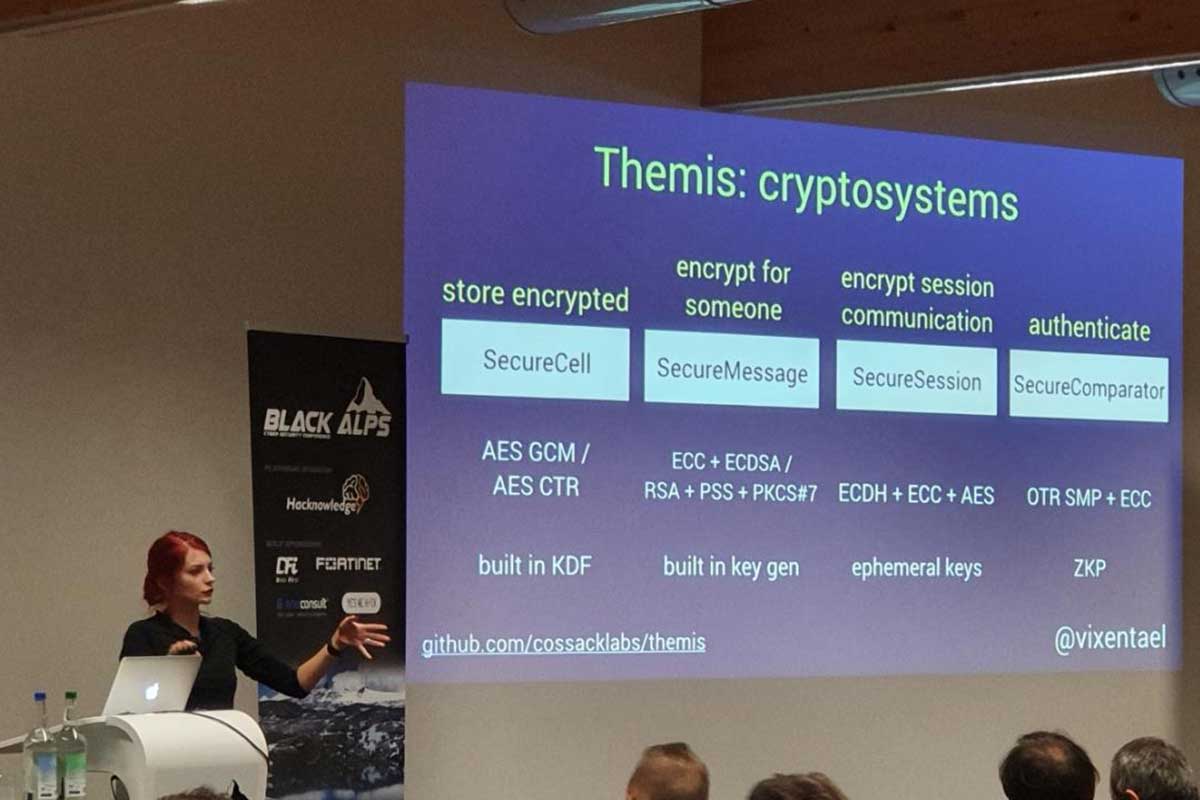
Maintaining cross-platform cryptographic library is a journey full of unexpected bugs, language-specific hacks, difficult decisions and endless struggle to make developer-facing APIs easy-to-use and hard-to-misuse.
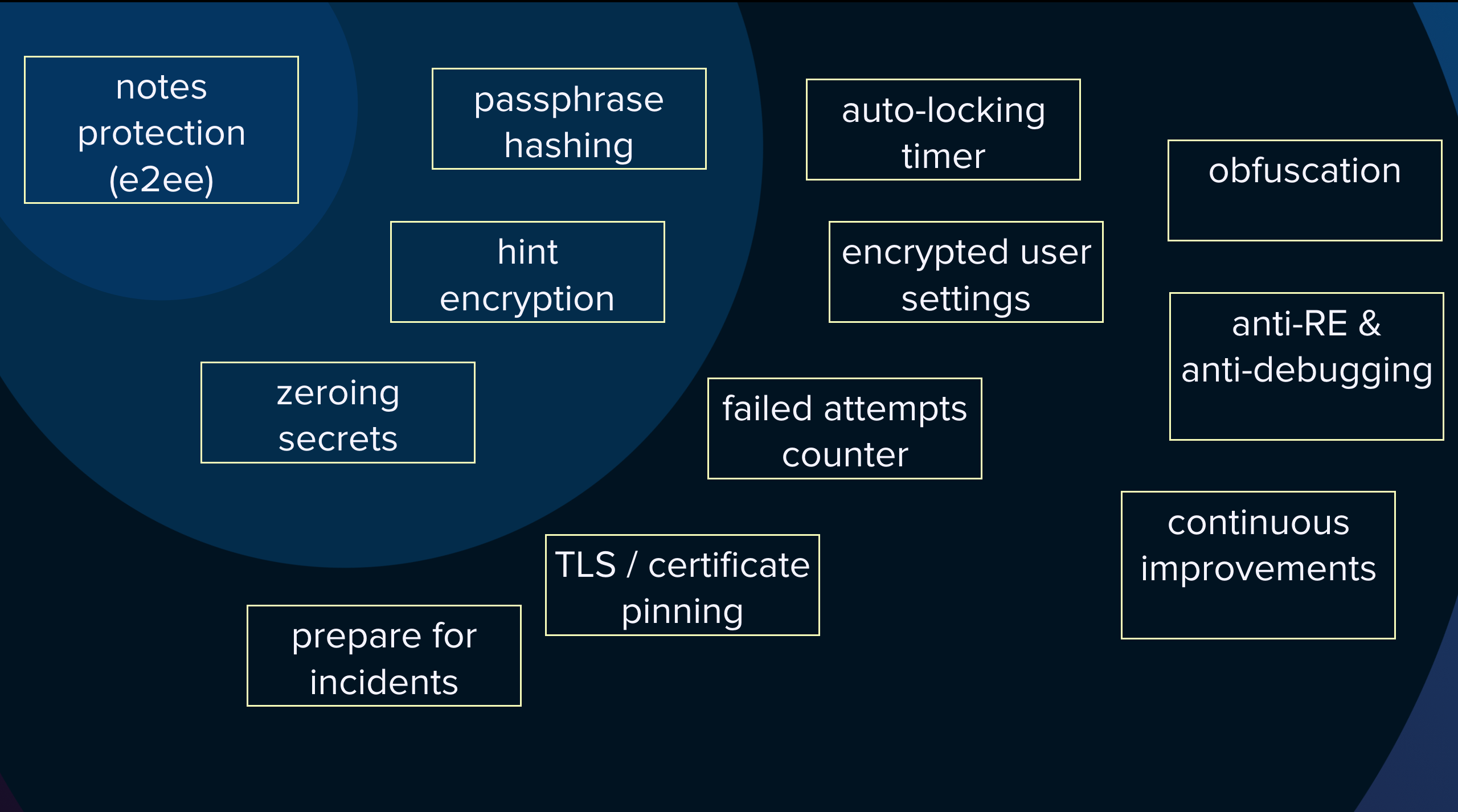
The real case about Bear note taking the app that decided to implement convenient note encryption and note locking for their existing user base.
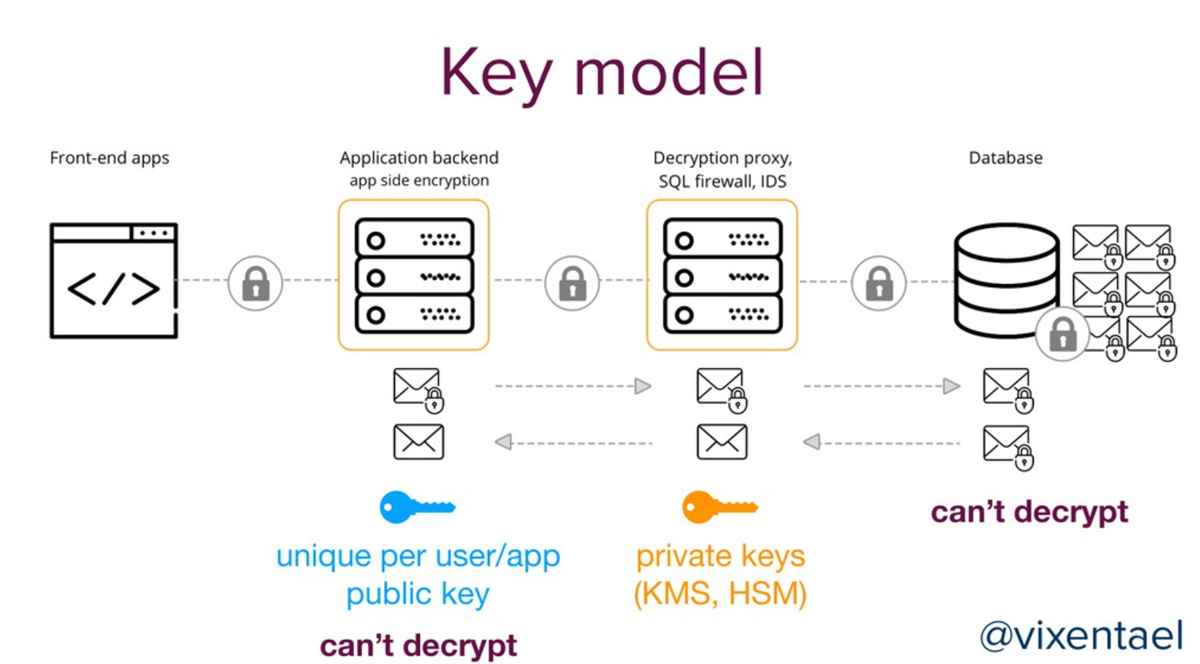
It comes to no surprise that any micro-services, any security controls you use to build applications – will eventually be broken (or fail).

Apple made many announcements on WWDC 2019 about cryptography, cybersecurity and privacy.

I was co-organizing CyberKids event during NoNameCon cyber security conference in Kyiv, Ukraine, May 2019.

Modern apps are multi-components, and most data leaks are caused by poor architectural decisions.

The essay I wrote for De Programmatica Ipsum magazine about secure software development and the mindset gap between the world of product makers and the world of security people.

In-depth technical inquiry about application-level encryption. How crypto helps to narrow down significant risks to controlled attack surfaces, enables managing the risk efficiently and elegantly, how tools and algorithms sit in a broader context of managing infrastructure-wide risks associated with handling sensitive data.

Before we get deep into protocols vulnerabilities: things you should remember designing your app flow from a security point of view.

This is a story of going through typical security challenges: how to build products that reliably deliver security guarantees, avoid typical pitfalls, and are usable in a predictable fashion by real users.

With intensifying threat access, snooping governments and insecure-internet-of-everything, the importance of zero-knowledge application architectures and end-to-end trust, for things more complicated than simple messaging, becomes more and more obvious for the app developers.

This is a story from a designer @anatinge and a developer @vixentael who worked together and built a product for people who really need it.

We will talk about building trust. Trust is built around various trust tokens: keys, passwords, secrets, biometric properties, things you have and things you know.